Realized Solutions uses a code protection technique called Dotfuscator, which is a tool used to protect our application code from hackers and unauthorized users.
The Dotfuscator is a third-party tool from Preemptive Solutions, shipped freely with Visual Studio, which obfuscates .NET applications.
What is obfuscation?
Code Obfuscation is the process of modifying an application to make it very difficult for an unauthorized party to decompile (convert from a compiled application back to human-readable source code) in order that they might make changes or steal, both of which are violations of the copyright and are illegal. After obfuscation, it is more difficult for a hacker to obtain the source code from an application, but the application itself remains fully functional. The obfuscation process may modify actual method instructions or signatures while leaving the functionality of the application the same.
What is the need to use code obfuscation?
To protect code from hackers and unauthorized users. It is very essential to do this process.
How does obfuscation work?
Code obfuscation consists of many different techniques that can complement each other to create a layered defense. Some obfuscation techniques are explained below.
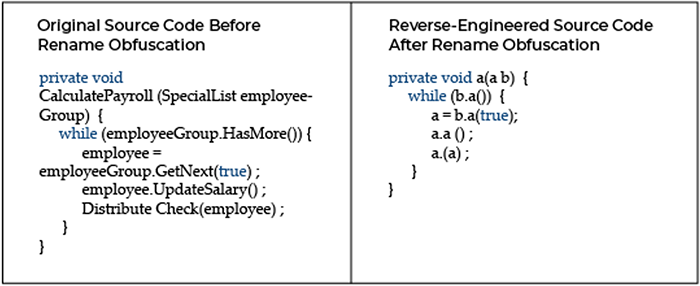
Rename Obfuscation:
Renaming technique alters the name of methods and variables. It makes the decompiled source harder for a human to understand but does not alter program execution.
String Encryption:
Even after renaming the method and variable names, the strings used inside the code would be readable. Strings can be used to locate critical code and can be the spot for the hacker to find the sensitive information. By using the string encryption technique, we can hide the string inside the executable code.
There are techniques like Control Flow Obfuscation, Instruction Pattern Obfuscation, Dummy Code Insertion, Unused Code and Metadata Removal and so on. Each layer adds on more dissimilarities to the new code compared to the original source code, and each difference makes the application more difficult to decompile.
For more information, please contact Realized Solutions to discuss how we can help you!




