When setting up a virtual network in Azure for an RSI client, there are a few different options we use to protect a client’s network. By default, Network Security Group (NSG) is created between objects and modified in various ways. Also, Azure Firewalls are used in conjunction with an NSG, but there are differences between the two important pieces within Azure.
Network Security Groups/ NSG’s are thought of as a basic allow/deny rule for each section of the virtual network. Rules are created to correspond with the network. For example, this virtual machine is allowed to communicate outwardly to the internet, but incoming traffic is denied. NSG doesn’t add any resources to the network but is only accessible through the OS 3-4 levels. The result is more common and generalized with their rules and protection. Another example, of what can be completed through NSG is to create a “deny rule” from the portal inwards preventing the Remote Desktop Protocol (RDP) from outside of the connections. This enables RDP on each Virtual Machine (VM) internally allowing access to individuals on the network.
Below is an example of how NSG’s is used to protect access to the virtual network from the internet and allow RDP to an individual Azure VM through Bastion.
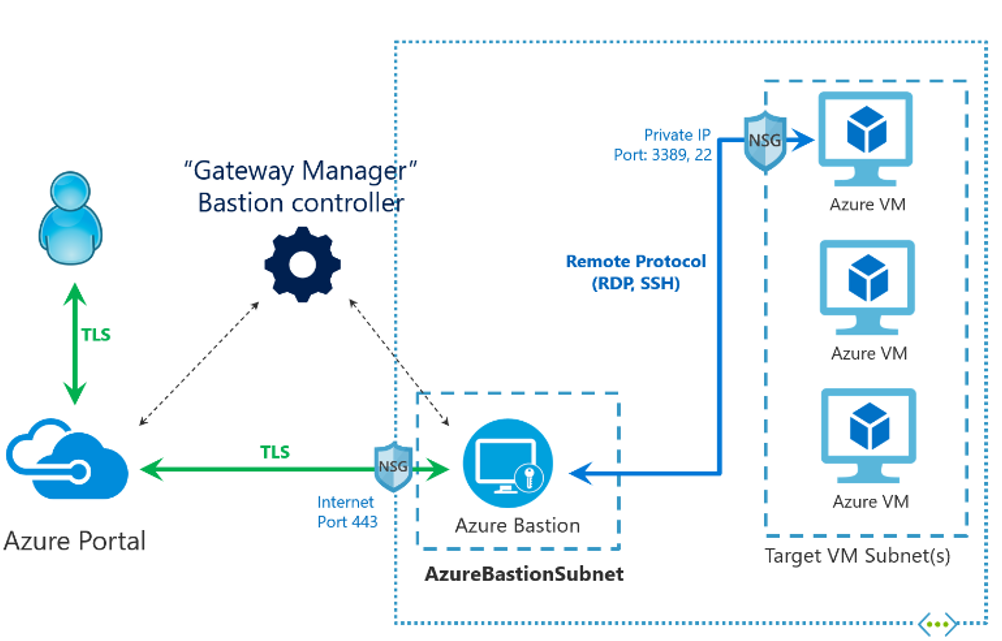
Then a client is also able to utilize the Azure Firewall which functions much like a normal firewall, and as mentioned above will work in conjunction with NSG. The Azure Firewall is fully managed and provides advanced security. By implementing the Azure Firewall, a client may experience a small increase in price but by a client putting Azure Firewall in place its automatically providing a higher value and level of support and security. Azure Firewall is compatible on the OS 3-7 levels, and instead of providing broad accept/deny protections, Azure Firewall zeros in by the minute to adjust and allow certain IP addresses, block individual websites, regions, and even recognize events like DDoS attempts. NSG limits filter traffic at the network level, but Azure Firewall provides detailed support using FQDN tags, source and destination masking, threat intelligence-based filtering to ensure the network is protected from cyber threats.
When comparing both options, NSG and Azure Firewall both need to be used in conjunction for the best result. The Azure Firewall will incur a small cost and NSG can be setup securely with an experienced administrator such as RSI. Nothing will beat the combination of both NSG and Azure Firewall security measures.




